Enderman
https://enderman.ch
https://youtube.com/endermanch
Community chat: https://t.me/hamster_kombat_chat_2
Website: https://hamster.network
Twitter: x.com/hamster_kombat
YouTube: https://www.youtube.com/@HamsterKombat_Official
Bot: https://t.me/hamster_kombat_bot
Last updated 11 months, 1 week ago
Your easy, fun crypto trading app for buying and trading any crypto on the market.
📱 App: @Blum
🤖 Trading Bot: @BlumCryptoTradingBot
🆘 Help: @BlumSupport
💬 Chat: @BlumCrypto_Chat
Last updated 1 year, 4 months ago
Turn your endless taps into a financial tool.
Join @tapswap_bot
Collaboration - @taping_Guru
Last updated 11 months, 3 weeks ago

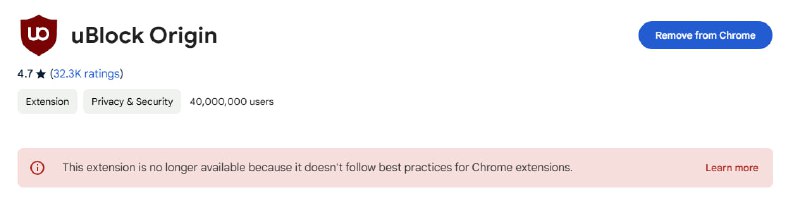
*🚫 uBlock Origin: Outlaws*
Some users are reporting uBlock Origin is no longer available for them.
The moment uBlock Origin gets killed by Google, Google Chrome will die a very painful death. We've almost reached that point of no return.
CS:GO gamers assemble

Please ask your questions in the comments if you have any. Also just in case, I am not suicidal.
?????
The VPN servers only differ by their protocol. So, the suggestions off the top of my head are WireGuard, OpenVPN, Outline. You'll need to read a lot and understand the UNIX terminal basics. There's a single one-click automated option I know of right now — AmneziaVPN. It's completely free, open-source and based on WireGuard. It uses Docker to completely automate the process, which allows even your grandma to set it up quickly and painlessly. It also offers options for when the state goes hog wild and blocks connections per protocol. (It's a thing in ?? / ??)
? Advanced VPNs. When the state goes rogue as described above, the protocols separate out into three categories:
▪️ Easily detectable: all common VPN tunnel protocols — WireGuard, OpenVPN, and so forth... They can be easily regulated by the state.
▪️ Detectable: commonly obfuscated versions of the common VPN tunnel protocols, e.g. AmneziaWG (WG + garbage packet spam during handshake initiation), OpenVPN over Cloak, Shadowsocks. They require much more scrutiny to be sifted out by the censorship systems.
▪️ Undetectable: while in reality not 100% safe, they're state-of-art as of September 2024 and make it past the Great Firewall of China. Most of these protocols aren't documented in English. If you live outside ??, ?? or ??, you likely won't need those for at least the next decade.
Let's go over them anyway. There's no nomenclature for them, but I'll try my best to sort them:
▪️ VMess
▪️ VLess
▪️ Naive
▪️ Trojan
▪️ Hysteria
The whole idea behind those «undetectable» protocols is to mask your VPN traffic as HTTPS (aka browsing a random web page). It is considerably slower than any of the VPN solutions shown before, but if there isn't any other option, that's what you're left with. Recent advancements include Xray + XTLS-REALITY, which has an ability to defeat Active Probing — previously uncontested state censorship method.
The bottom of the barrel, where everything above fails:
▪️ KCP
▪️ Meiru
▪️ TUIC
▪️ Brook
▪️ Pingtunnel — masks your traffic under ICMP! (pretty promising)
Umm, yea. You probably won't ever need those. But keep that in mind, there's no way to censor the internet.
? DNS. It's a very important subject, because a DNS (Domain Name System) server is what resolves domain names into IP addresses for you, and censorship can also be applied to it.
That's what DNS does, and you can manually resolve domains using the nslookup utility, for instance:
```
C:\Windows\System32>nslookup google.com
Server: AX4200.lan
Address: fd21:4bd3:61a3::1
Non-authoritative answer:
Name: google.com
Addresses: 2a00:1450:4010:c0a::8b
2a00:1450:4010:c0a::66
2a00:1450:4010:c0a::65
2a00:1450:4010:c0a::8a
173.194.221.138
173.194.221.113
173.194.221.100
173.194.221.101
173.194.221.102
173.194.221.139
```
DNS is just like a hash-table, a dictionary of the Internet:
x.com → 104.244.42.129 A
google.com → 108.177.14.139 A
Chances are you are using a DNS server provided by your ISP free of charge. Let's say the state asked the ISP to block shitter.com. The ISP might restrict access to that resource via DPI, but it also might resolve the domain name to localhost, or some RFC-private IPv4, 10.0.0.0/8 for instance.
In the best case scenario you can directly set custom DNS servers (1.1.1.1, 1.0.0.1 — CloudFlare; 8.8.8.8, 8.4.4.8 — Google) either network-wide or per device. Problem solved. However, this might not work! An ISP may very well hijack your DNS requests server-side and redirect them to their DNS server. Or, they could just block any outgoing UDP traffic on the port 53 when their servers aren't listed as an endpoint.
The solution to both of these digital rape cases is DNS over HTTPS or DNS over TLS. Now the idea is strikingly similar to that in the «undetectable» VPNs. The tools are also open-source and freely available, I'll list them here (OpenWRT packages as an example):
▪️ HTTPS-DNS-proxy
▪️ DNSCrypt-proxy
▪️ Stubby
*? why are .com extensions applications supporting 64 bit tho???*
The biggest misconception about files in Windows is that extensions are important, and somehow define whether the file runs or not. In reality, extensions are purely cosmetic. You can register parsers for your very own extensions within the registry (HKLM\Software\Classes ← HKCR) and set verbs and rules for Windows Explorer to follow when it stumbles upon your file association. That's the whole idea of extensions in Windows — to let Windows Shell automate passing the file over to the executable for you. There are protocols too, which Microsoft seem to be more fond of lately... (hello, Android content providers?)
No matter the extension, the contents of the file remain the same, and if the file has executable contents within it, you can run it. In fact, I suggest you try changing the extension of any executable you wish to .jpg and then run that JPEG-file from a command line.
The only difference for «executable files» in Windows is that they are the command that runs upon execution. NoEscape (does anyone even remember that?) leverages the registry nature of the executable file association. It sets up a pass-through executable that runs malicious code, but then follows up with running the original executable. Sneaky. It's called a companion virus. Neshta.A is a great example too.
Shell extensions are sort of similar in fashion. You can check my blog post out if you want to know the basics.
Community chat: https://t.me/hamster_kombat_chat_2
Website: https://hamster.network
Twitter: x.com/hamster_kombat
YouTube: https://www.youtube.com/@HamsterKombat_Official
Bot: https://t.me/hamster_kombat_bot
Last updated 11 months, 1 week ago
Your easy, fun crypto trading app for buying and trading any crypto on the market.
📱 App: @Blum
🤖 Trading Bot: @BlumCryptoTradingBot
🆘 Help: @BlumSupport
💬 Chat: @BlumCrypto_Chat
Last updated 1 year, 4 months ago
Turn your endless taps into a financial tool.
Join @tapswap_bot
Collaboration - @taping_Guru
Last updated 11 months, 3 weeks ago