road to OSCP
Бизнес блог #1
Выжимаю книги до самой сути.
👉 Реклама - @jaMasha
📇 Хотите свою книгу? Мы напишем её за вас и сделаем книгу бестселлером. Подробности в боте @Summary_library_bot
🏆 Оставьте след в истории с помощью книги
https://expert-book.pro
Фильмы и сериалы со всей планеты. Мы знаем, что посмотреть, где посмотреть и на что сходить в кино.
Last updated 2 days, 8 hours ago
Все материалы размещены по партнёрской програме ivi.ru | All materials are posted on the partner program ivi.ru
По всем вопросам: @kuzr103
Купить рекламу: https://telega.in/c/k1noxa103
Основной канал: https://t.me/kino_hd2
Last updated 1 month, 2 weeks ago
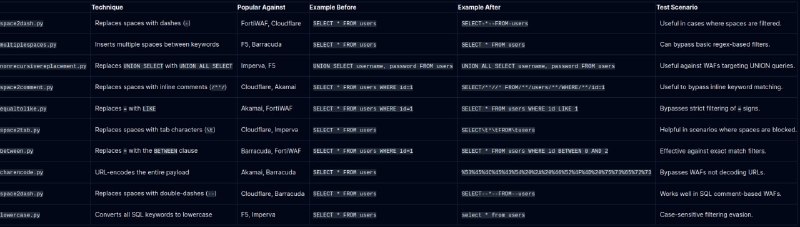
Ways to use templates in SQL-map to bypass WAFs from vendors like FortiWAF, F5, Barracuda, Akamai, Cloudflare, and Imperva

Gotta cache 'em all: bending the rules of web cache exploitation
This article examines the behavior of different HTTP servers and proxies when parsing specially crafted URLs. It also introduces techniques that exploit parser discrepancies, enabling arbitrary web cache poisoning and deception across numerous websites and CDN providers.
JS to find endpoints on a site in HTML code, in the developer console execute:
javascript:(function(){var scripts=document.getElementsByTagName("script"),regex=/(?<=(\"|\'|\`))\/[a\-zA\-Z0\-9\_?&=\/\\-\\#\.]*(?=(\"|\'|\`))/g;const results=new Set;for(var i=0;i<scripts.length;i++){var t=scripts[i].src;""!=t&&fetch(t).then(function(t){return t.text()}).then(function(t){var e=t.matchAll(regex);for(let r of e)results.add(r[0])}).catch(function(t){console.log("An error occurred: ",t)})}var pageContent=document.documentElement.outerHTML,matches=pageContent.matchAll(regex);for(const match of matches)results.add(match[0]);function writeResults(){results.forEach(function(t){document.write(t+"<br>")})}setTimeout(writeResults,3e3);})();
Today, we'll talk a bit about JavaScript recon in web applications. I've based my methodology on My Javascript Recon Process - BugBounty.
Collecting links to JS files can be done using gau:
```
gau example.com | grep -iE '.js' | grep -ivE '.json' | sort -u >> exampleJS.txt
```
Alternatively, you can use waymore, which seems to be better:
```
python3 waymore.py -i example.com -ko ".js(\?|$)"
```
We can also try fuzzing to find hidden JS files:
```
ffuf -u https://www.example.com/js/ -w jsWordlist.txt -t 200
```
The wordlist for fuzzing can be found here: https://wordlists.assetnote.io/
After that, ping the JS links as some of them may be outdated.
```
httpx -l exampleJS.txt -mc 200
```
Now, let's look for secrets in these files using SecretFinder, a tool for detecting sensitive data such as apikeys, accesstokens, authorizations, jwt, etc. in a JS file:
```
cat exampleJS.txt | xargs -n2 -I @ bash -c 'echo -e "\n[URL] @\n";python3 SecretFinder.py -i @ -o cli' >> exampleJsSecrets.txt
```
Next, using availableForPurchase.py, we can check if the domains referenced in the JS files are available for purchase. This tool, combined with linkfinder and collector, is really powerful. Sometimes developers make mistakes when writing a domain, possibly the domain imports an external JavaScript file, etc.
cat exampleJS.txt | xargs \-I @ bash \-c 'python3 linkfinder.py \-i @ \-o cli' | python3 collector.py output
cat output/urls.txt | python3 availableForPurchase.py
[NO] www.googleapis.com
[YES] www.gooogleapis.com
After executing the above command, a list of potential endpoints that were discovered in the JS becomes available for review:
cat output/paths.txt
We can also immediately check for subdomain takeover using subzy
```
cat output/urls.txt |grep "https{0,1}://[^/].example.com/[^ ]" >> subdomainExample.txt; subzy run --targets subdomainExample.txt
```
Also, excellent extensions for Burp:
JS Miner and JS Link Finder which perform similar tasks but in real-time, for greater coverage it's better to use both script scanning and plugins
Бизнес блог #1
Выжимаю книги до самой сути.
👉 Реклама - @jaMasha
📇 Хотите свою книгу? Мы напишем её за вас и сделаем книгу бестселлером. Подробности в боте @Summary_library_bot
🏆 Оставьте след в истории с помощью книги
https://expert-book.pro
Фильмы и сериалы со всей планеты. Мы знаем, что посмотреть, где посмотреть и на что сходить в кино.
Last updated 2 days, 8 hours ago
Все материалы размещены по партнёрской програме ivi.ru | All materials are posted on the partner program ivi.ru
По всем вопросам: @kuzr103
Купить рекламу: https://telega.in/c/k1noxa103
Основной канал: https://t.me/kino_hd2
Last updated 1 month, 2 weeks ago