Linux Kernel Security
Community chat: https://t.me/hamster_kombat_chat_2
Website: https://hamster.network
Twitter: x.com/hamster_kombat
YouTube: https://www.youtube.com/@HamsterKombat_Official
Bot: https://t.me/hamster_kombat_bot
Last updated 11 months, 1 week ago
Your easy, fun crypto trading app for buying and trading any crypto on the market.
📱 App: @Blum
🤖 Trading Bot: @BlumCryptoTradingBot
🆘 Help: @BlumSupport
💬 Chat: @BlumCrypto_Chat
Last updated 1 year, 4 months ago
Turn your endless taps into a financial tool.
Join @tapswap_bot
Collaboration - @taping_Guru
Last updated 11 months, 3 weeks ago

SLUBStick: Arbitrary Memory Writes through Practical Software Cross-Cache Attacks within the Linux Kernel
A paper by Lukas Maar, Stefan Gast, et al. about exploiting slab memory corruptions via a cross-allocator slab-to-page attack targeting user page tables.
The paper covers:
— Using a timing side-channel to make sure that all objects in a slab are under the exploit's control to increase the success chance of executing a cross-cache or a cross-allocator attack;
— Converting limited slab memory corruptions to a stronger slab use-after-free write primitive;
— Using a single-shot slab use-after-free write to gain control over user page tables and thus obtain physical memory arbitrary read/write.

To Boldly Go Where No Fuzzer Has Gone Before: Finding Bugs in Linux' Wireless Stacks through VirtIO Devices
A paper by Sönke Huster et al. about externally fuzzing the Linux kernel's Wi-Fi and Bluetooth stacks.
The implemented VirtFuzz fuzzer injects Wi-Fi and Bluetooth frames into the kernel through QEMU via a custom VirtIO-based device. The fuzzer also collects coverage via KCOV-based annotations and exposes it to the host via QEMU's shared memory device to guide the fuzzing process.
64 bytes and a ROP chain – A journey through nftables
A two-part article by Davide Ornaghi about finding, analyzing, and exploiting a stack buffer-overflow in the netfilter subsystem from the softirq context.
Davide also gave a talk (slides) about this work at HITB Amsterdam last year.
Betrusted
64 bytes and a ROP chain - A journey through nftables - Part 1
Dive into the process of vulnerability research in the Linux kernel: focus on CVE-2023-0179 and Local Privilege Escalation (LPE).

Make your own backdoor: CFLAGS code injection, Makefile injection, pkg-config
Vegard Nossum posted a PoC backdoor for the Linux kernel that doesn't require changing the kernel source code or any release tarballs.
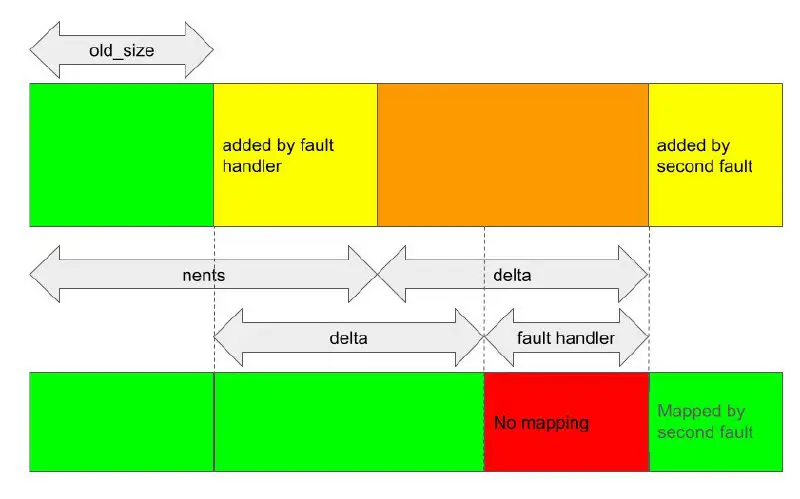
Gaining kernel code execution on an MTE-enabled Pixel 8
An article by Man Yue Mo about exploiting a race condition in the JIT memory regions handling code in the Mali GPU driver.
The shared exploit disables SELinux and gains root privileges from the untrusted_app context on Pixel 8.
In the article, the author also pointed out that MTE (Memory Tagging Extension) does not prevent the exploitation of this bug, as invalid memory accesses happen through the GPU coprocessor.

Mali GPU Kernel LPE
An article by simo about expoiting a kernel pointer leak and an out-of-bounds write bug in the Mali GPU driver.
The shared exploit leverages the pipe_buffer structure to gain arbitrary read/write to disable SELinux and gain root privileges on Pixel 7 and 8 Pro phones.
In the article, the researcher also pointed out the non-transparent and confusing handling of reported vulnerabilities by Google.

SyzRetrospector: A Large-Scale Retrospective Study of Syzbot
Joseph Bursey, Ardalan Amiri Sani, and Zhiyun Qian published an article analyzing how changes in the Linux kernel and syzkaller influence the ability of syzbot to find bugs.
In the paper, the researchers share the key results of their analysis and offer suggestions on how to improve the syzbot effectiveness.
Linux Kernel GSM Multiplexing Race Condition Local Privilege Escalation Vulnerability (CVE-2023-6546)
An article by Nassim Asrir about exploiting a race condition that leads to a kmalloc-1k use-after-free in the n_gsm TTY line discipline module.
In the exploit, the researcher overwrote the freed object, gained an arbitrary function call with a controlled argument primitive, and escalated privileges by spawning a userspace process via run_cmd.
The exploit bypasses KASLR by leaking the kernel address from world-readable /sys/kernel/notes. This is a separate vulnerability that still affects up-to-date kernels that enable CONFIG_XEN_PV.
To bypass SMAP, the author used a novel technique of filling the kernfs_pr_cont_buf global variable with controlled data from userspace. The data is supplied as the path to a cgroup filter created via iptables, whose use requires unprivileged user namespaces.
The repository with the exploit also contains a set of scripts for automatically extracting symbol offsets for Ubuntu, CentOS, and RHEL kernels.
GitHub
GitHub - Nassim-Asrir/ZDI-24-020
Contribute to Nassim-Asrir/ZDI-24-020 development by creating an account on GitHub.

Community chat: https://t.me/hamster_kombat_chat_2
Website: https://hamster.network
Twitter: x.com/hamster_kombat
YouTube: https://www.youtube.com/@HamsterKombat_Official
Bot: https://t.me/hamster_kombat_bot
Last updated 11 months, 1 week ago
Your easy, fun crypto trading app for buying and trading any crypto on the market.
📱 App: @Blum
🤖 Trading Bot: @BlumCryptoTradingBot
🆘 Help: @BlumSupport
💬 Chat: @BlumCrypto_Chat
Last updated 1 year, 4 months ago
Turn your endless taps into a financial tool.
Join @tapswap_bot
Collaboration - @taping_Guru
Last updated 11 months, 3 weeks ago
